It seems that dangerous phishing emails has become a regular to many inboxes.
What: a business contact and friend of mine had his business email account “cleverly hacked” (his words, whatever that means). As a result, I received a dangerous phishing email.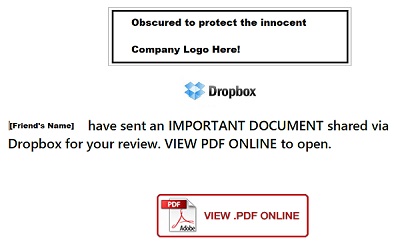
Clicking to “VIEW .PDF ONLINE” took the recipient to page that emulated a DocuSign.com document sharing page, and requested that you login to an email account to access the “shared document.”
The goal of the phishing attack, of course, was to collect email address and password combinations.
Normally suspicious
I am normally suspicious and consider myself to be quite circumspect with regard to online dangers. However, this email from a trusted business contact and friend caught me totally off-guard. I didn’t bother to check the URL before entering the requested information in order “to access the document” my friend had sent me. The phishing screen captured my login information and then promptly notified me that my “email or password were incorrect.”
Only then did I look carefully at the URL, only to discover that the URL was baicaio.bid (a domain registered under an intentionally obfuscated name with a Panama address).
I took immediate action and changed my password on the account I had foolishly used in my attempt to fetch the document I thought was coming from my friend.
Normally safe
I consider my approach to password management to be quite safe.
- Almost all of my passwords—to more than 100 sites—are unique. I almost never repeat passwords from site-to-site.
- Almost all of my passwords are complex—containing combinations of upper and lower case letters, numbers, and symbols (where the sites permit)
- My passwords range in length from eight (8) characters and up. Sites holding critical personal and financial data employ complex passwords with twelve (12) or more characters.
I keep track of all of these using LastPass.
This is a FREE SERVICE that generates complex passwords for you, stores them securely, and makes them readily accessible for your use across multiple devices—including desktop browsers and applications, and other smart devices (such as my Moto Z Force Droid Android device). I never get concerned about remembering a complex password. Life is both SAFE and SIMPLE.
Protecting others
I like to think, in doing this, that I am protecting, not only myself, but my family (from potential financial loss and other risks stemming from identity theft) and my friends (who might otherwise suffer from spam or phishing attacks from my accounts).
I have chosen also to protect myself (and my family) by using LifeLock, too. My work requires me to conduct a lot of online business.
But, I am above 60 years in age now, so I also use LastPass Premium in order to make accommodations for my accounts after my decease. Two of my more technically-oriented children have been granted access to my LastPass account in the event something should happen to me where I am incapacitated.
The way this works is, when I am deceased or incapacitated, they can make a request to LastPass, as a “trusted party” to my account, to access my LastPass vault. If I do not deny the request within three (3) days, their access will be granted.
Once they have access, they can go in and close accounts on social media, or elsewhere, for me. I don’t leave a legacy of accounts to be hacked and abused in the future.
CyberSecurity is a Serius Matter
I’m writing this because I’d like you to consider your personal cybersecurity.
You should do this.
And, you should do it not just for yourself. You should do it to protect your family, your friends, and your business contacts from dangers that might arise from the hacking of your accounts.
Think about it. Do something about it. Contact RKL eSolutions cybersecurity team if you have questions about current threats or need help with your company's IT security.
Webinar: IT Backup & Recovery Planning
When: Jan 24th | Wednesday |2pm est | webcast
In this webinar, we will outline a few of the major areas that your business should consider in a risk assessment. including how to manage risk, mitigate risk, and how to use your IT back and recovery plan to a competitive advantage.




