Beware of suspicious emails posing as our employees
By now, most people are aware of phishing scams and how to recognize suspicious emails from unknown senders or emails that contain strange hyperlinks. But what happens when the email appears to be from a trusted contact with, what could be, a valid reason? Here’s an example of a real-world phishing scam, targeting customers like you from an imposter posing as me, Walter Goodfield!
The email below is real. It was forwarded to me by a customer of ours who suspected the email was a scam. Upon a closer look, there are seven items in this email that individually, are suspicious, but collectively are impossible to ignore as a scam. Let’s examine the evidence one-by-one.
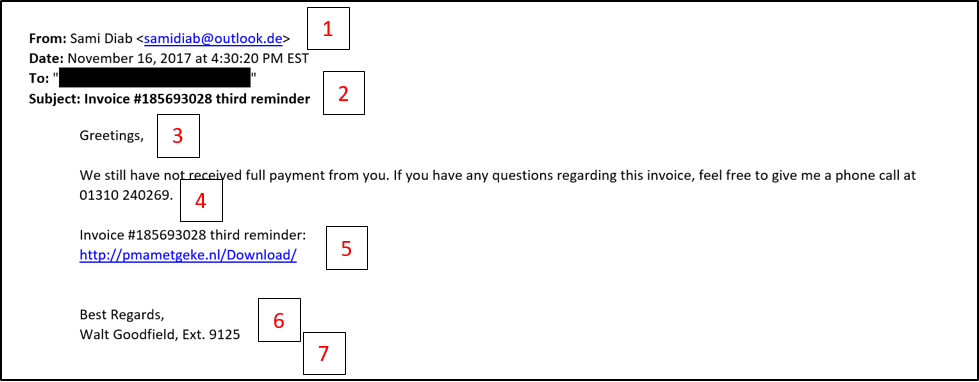
- The first indication that this may not be a credible email is the sender’s domain. You’ll notice that it is not from an RKL eSolutions domain and even has an international suffix. Be careful, though, some phishing scams hide the sender address and this obvious tip-off. You can always confirm the sender’s email address by reviewing the ‘full email header’ of your email service.
- In this email, the sender sends a bogus invoice number and ‘third reminder’ notice in the header. A simple search in your Sage Accounts Payable records should indicate that this invoice probably does not match any open invoices on account for RKL eSolutions.
- Typically, communications from RKL eSolutions will be personally addressed to the intended recipient. Very rarely would a team member from RKL eSolutions address our customers with such an impersonal email greeting.
- Another indicator that this may not be real is the international phone number. RKL eSolutions only operates with offices and team members in the continental US. For the sake of this blog, I tried to call the phone number and, unsurprisingly, it was not in service.
- It’s unlikely that RKL eSolutions would send an unsolicited email with a hyperlink to access information. While we do use DropBox, WebEx, GoTo Meeting, Online Bill Pay, and other online tools, the request to access these tools almost always originates with you, the end user. In some cases, our team may send attachments as supporting evidence in response to an inquiry, too. But again, these communications are not unsolicited.
- The signature line does not contain my contact information including company phone, mobile phone nor email address. A few years ago, RKL eSolutions standardized our employee auto signatures across the organization. Every email communication should be formatted as follows.

- All of our RKL eSolutions contain a standard legal disclosure at the end like:

If you’ve been a victim of this phishing scam or suspect that others in your organization have been, please follow these simple instructions.
- Notify your team. Alert your IT team and staff to be aware of this email scam and do not click on the hyperlink or open attachments.
- Forward the email directly to spam@uce.gov and reportphishing@apwg.org. You can also file a report with the Federal Trade Commission at gov/complaint
- Contact us if you or someone you know has either
- clicked on the links or shared sensitive information with someone other than an RKL eSolutions employee
- you suspect malware or ransomware has been installed on your network.
- If you’re uncertain about the email authenticity, call us.
The seven tips above were documented to help you identify the bogus data along with inconsistencies and to avoid falling victim to malicious attempts to access your information.
Webinar: IT Backup & Recovery Planning
What: In this webinar, we will outline a few of the major areas that your business should consider in a risk assessment. including how to manage risk, mitigate risk, and how to use your IT back and recovery plan to a competitive advantage.
When: Wednesday, Jan 24th | 2pm est, 11am pst
For More Cyber Security Blogs
Cybercrime Prevention Strategies
Cybercrime Prevention in Social Networking Websites
Cybersecurity Things You Should Know
Cybersecurity Assessment
RKL eSolutions IT Services team has several cybersecurity experts on staff should you have any further questions on how you can protect yourself.




