If you haven't already seen the images of long lines and closed gas stations in Virginia, Georgia and the Carolinas, you've probably at least heard that there has been a recent disruption in oil transportation on the East Coast. On May 7, 2021, the 5,500-mile-long Colonial Pipeline stopped operations, ceasing to carry nearly 3 million barrels of fuel per day between Texas and New York. So what caused the largest US oil pipeline to shut down so suddenly?
On May 7, 2021, the Colonial Pipeline Company learned it was the victim of a cybersecurity attack. They have since determined that the incident involved Ransomware. In an effort to contain the threat to their data, Colonial Pipeline took its systems offline, temporarily halting all pipeline operations. The uncertainty of when the pipeline would be back online led to rampant panic buying of gasoline across the Southeast, creating shortages at gas stations that could no longer refuel. Fortunately, the malware did not infiltrate the pipeline's operation system. Thanks to Colonial Pipeline's quick action to take operations offline and assess the situation, as of May 13, 2021, product delivery has restarted in the majority of markets.
Now, your company may not be responsible for fueling the majority of the East Coast, but Ransomware still poses a serious danger to your operations and could cripple your business for months. In the case of ransomware (and most types of malware), an ounce of prevention is worth a pound of cure. Let's take a look at how ransomware works and what you can do to proactively keep your company's data safe:
The Ransomware threat is real. A few statistics to start off (courtesy of Safe at Last):
- Ransomware perpetrators carry out more than 4,000 attacks daily.
- 1 in 3,000 emails that pass through filters contains malware.
- On average, organizations pay a ransom of $233,217.
- There’s a 19-day downtime following a ransomware attack.
- 95 new ransomware families were discovered in 2019.
- Ransomware attacks in the education sector rose by 388% between Q2 and Q3 of 2020.
- In 2021, ransomware attacks against businesses will occur every 11 seconds.
- The global cost associated with ransomware recovery will exceed $20 billion in 2021.
How do I get it?
Typically, ransomware is triggered by phishing emails. You receive an email that appears to be from a legitimate source, click a link, and you now have ransomware. The older versions of ransomware were often triggered immediately, and its effects were immediately observable by your computer slowing down and the hard drive light being constantly on.
What’s different now?
Today, once your computer is compromised, there is often no symptom. The bots of old have been replaced by talented IT technicians who will map your network, research every IP address, learn how your backups are managed and have as good a handle on your systems as your internal IT support. This process can take weeks or even over a month. Once they know all they need to know, they pull the trigger and encrypt all your files, delete all your backups and effectively shut down your business.
The ransoms have also gotten bigger; a few years ago, they were demanding $300 to $600, today they can demand and receive millions.
How can I prevent this?
#1. Practice Good Cyber Hygiene!
Before you click on a link, hover your mouse cursor over it and read where it’s about to take you. There are many options for training your employees to be more aware of phishing attempts.
#2. Use Complex Passwords.
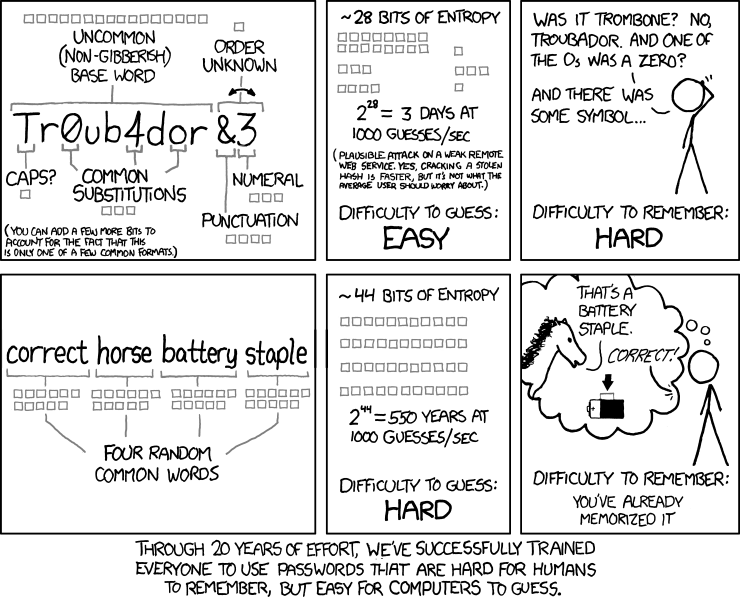
Password complexity may be simpler than you think it is. In this example, four random words from the dictionary are over 60,000 times more secure than a password like Tr0ub4dor&3 and easier to remember. Length is strength. The longer a password is, the less often it needs to be changed.
#3. Backup Your Systems Offline
If at all possible, have some offline backups. This can be difficult in the age of Terabytes, but if you can get to your backups, so can an intruder, and they will. Destruction of your backups is one of the top items on their checklist. There are not a lot of ways to create offline backups these days since we’re past the era of tape backups, but there are some technologies that will allow you to remove a copy of your data from the premises. There are also some tricks you can do with how and when to attach to your backup drives.
The larger your company is, the more attractive it is as a target of ransomware. Your absolute best defense is to have a complete offline backup and not pay the ransom. Depending on where the ransom is, it may even be illegal to pay; the FBI should be consulted for guidance.
For the latest updates on Colonial Pipeline's Operations Response to the incident, click here.