
Will your Credit Card Processing be affected when Paya discontinues support for TLS 1.0? We have pulled together this article in order to help you understand what this means and what steps you can take to help ensure you will not be affected by this change.
This article looks to address issues specific to companies that are using Sage 500 ERP (formerly Sage MAS 500), but some of the information could be used when looking to address issues with other solutions or with custom developed integrations to the Paya services.
Background
Paya is the integrated credit card solution for many Sage Accounting and ERP solutions. Recently, Paya has announced they would no longer support TLS 1.0 for Credit Card Transactions effective on June 1, 2018. This is in line with the Payment Card Industry (PCI) compliance guidelines that now indicate that only TLS 1.1 and TLS 1.2 (preferred) are to be utilized for credit card transactions. The PCI requirement is that Processors and Merchants discontinue the use of TLS 1.0 by June 30, 2018.
Details of these guidelines can be found at the PCI Security Standards Council website. Click here for an article that outlines this change in policy.
Note that while Paya had discontinued use of TLS 1.0 on June 1, 2018 they rolled back this change on June 6, 2018. Paya has now announced that they will discontinue the use of TLS 1.0 on June 25, 2018. This is ahead of the June 30, 2018 date required for PCI Compliance.
While overall the improvement to credit card security is a good thing, this may be an issue for companies that are operating on unsupported versions of their accounting software. If you are using an unsupported version of your accounting software, it is possible that the software publisher has not released an update to support these new guidelines. If you begin experiencing issues with credit card processing, you should reach out to your contacts at your Value Added Reseller for your Accounting/ERP solution. They can help you determine if this issue is related to the issues with TLS 1.0 and provide guidance on how to resolve this issue.
For companies that have built custom integrations to Paya, you will also want to review and ensure that your solution follows the new guidelines. This may require code changes. You can reach out to us if you have a custom application and need assistance with making it compliant with TLS 1.2.
What is TLS 1.0?
You might wonder what all this talk of TLS 1.0 is about and why it matters to you. Transport Layer Security (TLS) is a protocol that is used to securely transmit information over networks (this could be a local network or the internet). TLS 1.0 is a standard that was introduced in 1999. TLS 1.2 was introduced in 2008 and is the most current version of TLS available at this time. The Credit Card industry feels that it is important to discontinue use of TLS 1.0 and require processors and merchants to utilize either TLS 1.1 or TLS 1.2. Note that while TLS 1.1 is not affected by the current PCI requirements it will likely will be phased out in the future as well.
What do I need to do?
Originally it was thought that clients running Sage 500 ERP Version 2013 (aka 7.5) or later would not have any issues or require changes to their environment when use of TLS 1.0 was discontinued by Paya. This was due to the fact that Paya had introduced the Sage Exchange Desktop (aka SED) 2.0 which provided an update to utilize TLS 1.2. SED was introduced with Sage 500 ERP starting with the 2013 version and has been used in all future versions. While this does address the primary issue of credit card transaction processing, we have found that it does not address the ability to Settle Credit Card Transactions in Sage 500 ERP. This task continues to utilize the original integration to Paya that used Web Service calls. Because this task is not using SED, it appears that many companies are having issues once TLS 1.0 is disabled by Paya.
We have found that for a large percentage of our clients the three items below will address and resolve the issues with Sage 500 ERP when Paya discontinues support for TLS 1.0. This information was gathered during the six day window when Paya initially disabled TLS 1.0 on their servers. Unfortunately, there will be no way to verify your configuration is working until Paya disables this again later this month.
This information is provided as is. We highly recommend that before you make these changes to your production environment, that you implement the changes in a test environment. While Paya does not provide a test environment to validate that your changes are successfully utilizing TLS 1.2, you can ensure that the changes you are introducing to your environment will not have a negative impact on any other applications. This is important as many applications utilize TLS for network communication. As an example, the Sage 500 ERP client utilizes TLS 1.0 to communication to SQL Server. If you have any questions or concerns, we recommend that you reach out to your software support provider to review and discuss before making any changes.
Steps to address issue:
- Windows Updates – Ensure that your workstations and servers are current on all Windows Updates. Paya has indicated that there are several Windows Security Updates that are required for their update to TLS 1.2. These will be listed later in this article, but the simplest approach is to ensure all updates are applied.
- Note that you must reboot after applying updates, so ensure that after any updates are complete that you have also rebooted the workstation or server that is use for credit card processing.
- SED 2.x – Sage Exchange Desktop 2.0 was introduced by Paya to provide support for TLS 1.2. If you are still running SED 1.x, we suggest you reach out to your software provider to discuss this.
- Windows Registry Entry – Based on research that the RKL team completed, we have found that a Windows Registry Entry will force the Paya integration to utilize TLS 1.2 instead of TLS 1.0. Details of this entry are provided below. This should be completed by someone familiar with the Windows Registry and changes to the Windows registry can cause unexpected issue.
- This change provides a solution for the Paya Web Service Integration that was in use on Sage 500 ERP version 7.4 as well as for the Settle Credit Card Transactions task in version 2013 (aka 7.5) and after.
Windows Updates
Please check with IT support if you are unfamiliar with Windows Updates and how to review them.
Checking the Version of SED:
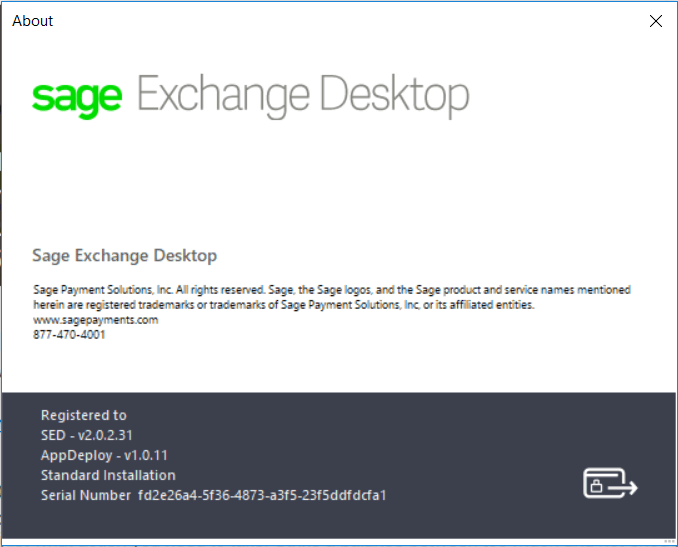
If you are using Sage Exchange Desktop, you can check the version you are running by reviewing the About Sage Exchange Desktop by launching this from the System Tray on your Windows Taskbar. An example of this is provided for you below.
Sage Exchange Desktop version 2.0.2.31 is shown here:
Windows Registry Entry
We have found that a new registry entry is required in order for the Paya Web Services integration to communicate utilizing TLS 1.2 instead of TLS 1.0. This entry is different for 64-bit machine and 32-bit machines. We have provided the detailed steps for adding the registry entry on a 64-bit machine, but provided the name of the key for 32-bit machines as well. The steps are the same, the registry Key is the only difference.
On 64-bit machines the new registry entry is:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319
On 32-bit machines the new registry entry is:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319
Follow these steps to add this registry entry:
1. Launch Registry Editor on your Windows machine
2. Navigate to the correct Registry Key (see screen shot below)
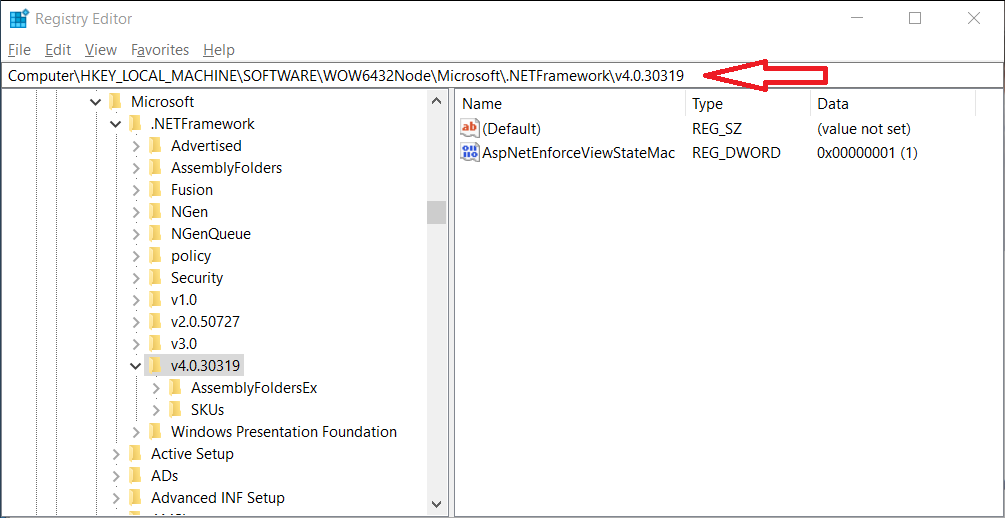
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\.NETFramework\v4.0.30319
3. Add a new Value to this Registry Key by right clicking on the folder Key value
- Select New > DWORD (32-bit) Value
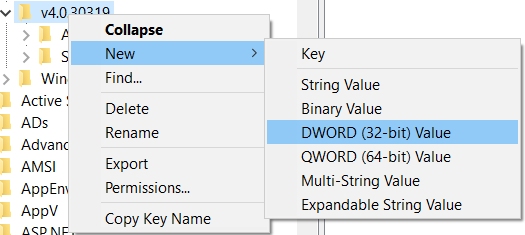
- Assign the name as SchUseStrongCrypto
- Once created, right click to Modify the value
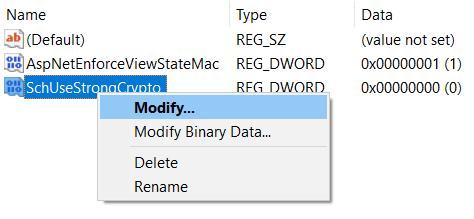
- Assign the value as 1 and click OK.
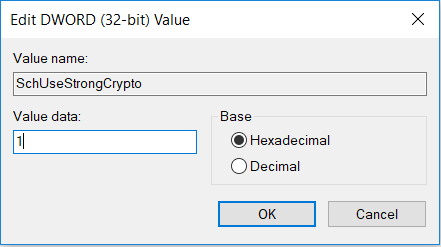
- When Complete, your registry entry should look like this:
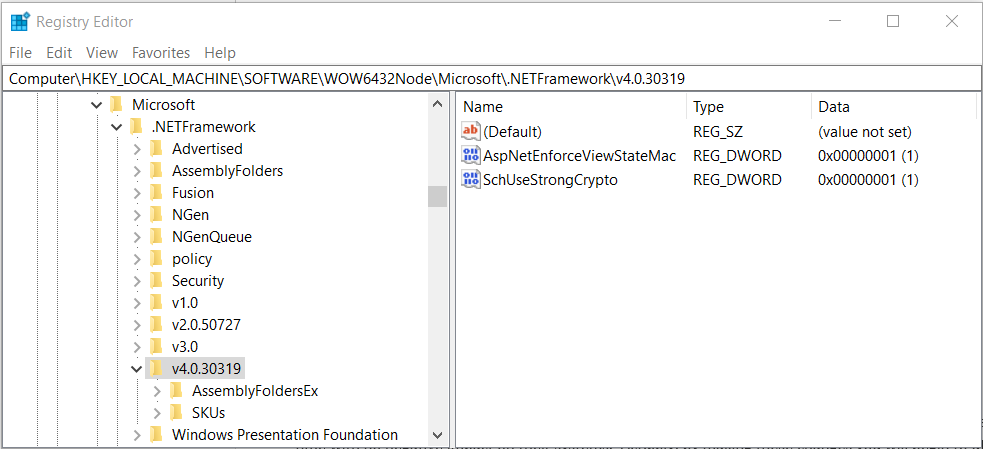
- Close the Registry Editor
When should I make these changes?
While these changes are not required until Paya discontinues TLS 1.0, we have found that clients can apply these changes ahead of time with no negative impact on their systems. By making these changes you will begin to utilize the more secure TLS 1.2. So, you will be in compliance with the PCI requirement even before Paya has completed their changes.
Disclaimers:
These updates have been tested with Sage 500 ERP versions 7.4, 2013 (7.5), 2014 (7.6), 2016 (7.7) and 2017 (7.8). Sage 500 ERP version 7.3 requires a source code modification. RKL has worked with clients to complete this update. Please reach out if you need assistance with this.
As all environments can be different we highly recommend that you test any changes prior to implementation on you production environment. We have not done exhaustive testing, so you will need to validate that your environment is not affected by these changes. We have successfully utilized the approach listed above for clients using Windows Server 2008R2, Windows Server 2012, Windows 7 Workstations, and Windows 10 Workstations. Our test were all with 64-bit machines
Again, we cannot stress enough that these updates should be applied to test environment first so that other 3rd party applications can be validated prior to deployment to production.
Paya Information
Paya has provided some information during the course of this effort. Here are the items they provided and comments from the RKL experience with these items. Again, all environments are different and some of these changes may be required for your environment.
We would recommend checking the Paya site if you are having issues with your credit card processing. Paya does provide Maintenance and Service Alerts. Here is a link to their Knowledgebase article:
https://support.paya.com/44510-knowledgebase/308786-maintenance-and-service-interruption-alerts
An example of the notification that was posted by Paya on their site is shown below:
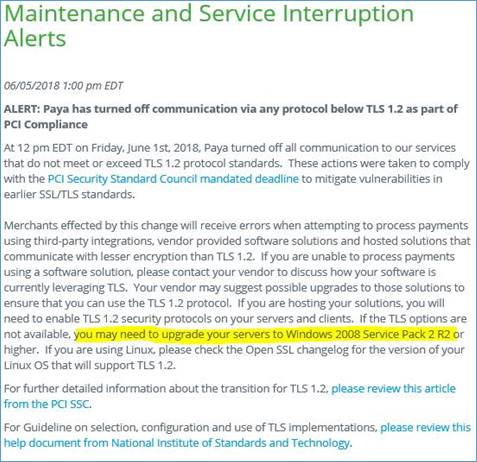
Paya Support and SED Download
Below are links for Paya Support as well as link to the SED 2.x download page.
- Paya Support/Knowledgebase - https://support.paya.com/
- Sage Exchanged Desktop 2.x download – https://www.sageexchange.com/install/#/sedv2x/en
Windows Updates
As noted above when discussing the Windows Updates, Paya has indicated some specific Windows Updates that are required for TLS 1.2. We have not attempted to install only the specific updates noted below, instead we have recommended to our clients that they apply all pending windows updates if they have not already done so. This has worked for our clients. However, as there may be situations when all updates cannot be applied, we are providing these for your reference.
The following KB articles provide the information on required patches:
- KB3154518 – Reliability Rollup HR-1605 – NDP 2.0 SP2 – Win7 SP1/Win 2008 R2 SP1
- KB3154519 – Reliability Rollup HR-1605 – NDP 2.0 SP2 – Win8 RTM/Win 2012 RTM
- KB3154520 – Reliability Rollup HR-1605 – NDP 2.0 SP2 – Win8.1RTM/Win 2012 R2 RTM
- KB3156421 -1605 HotFix Rollup through Windows Update for Windows 10.
Registry Entries
Paya provided the below suggested registry settings. We are including them for your reference. However, to date we have found no benefit in applying these for our clients. Only the registry entry noted above has appeared to provide the desired functionality. As noted above in this article, Sage 500 ERP requires that TLS 1.0 is enabled in order to allow the client to communicate with the server. Therefore disabling TLS 1.0 will affect your ability to use Sage 500 ERP.
Windows Registry Entries/Updates
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\WinHttp
"WinHttp"=dword:00000800
"SecureProtocols"=dword:00000800
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Internet Settings
"WinHttp"=dword:00000800
"SecureProtocols"=dword:00000800
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings
"WinHttp"=dword:00000800
"SecureProtocols"=dword:00000800
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0]
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"DisabledByDefault"=dword:00000000
"Enabled"=dword:00000001
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.1\Client] "DisabledByDefault"=dword:00000001
"Enabled"=dword:00000000
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Client]
"DisabledByDefault"=dword:00000001
"Enabled"=dword:00000000



